EXPOSE Network Series
Part 1 : – Introduction to the EXPOSE Network and its Hub, the Open Information Partnership (OIP).
Part 2 : – Examining the role of the EXPOSE network and authenticating the supporting evidence.
Part 4 : – Research into the EXPOSE Network partners and the web of globalist institutions behind them.
Part 5 : – Continuing to look at the EXPOSE Network partners and the web of globalist institutions behind them.
Part 6 : – The global funding streams and parallel international initiatives placing the EXPOSE Network inside a larger multinational operation.
The EXPOSE Network Facilitator
In June 2018, the Foreign and Commonwealth Office’s (FCO) Counter Disinformation and Media Development (CDMD) program issued their final scoping report for the the proposed EXPOSE Network. It established the role of a Network Facilitator to act as the central coordinator for the EXPOSE network of civil society organisations (CSO), non governmental organisations (NGO), fact checkers, smaller civil activists groups, journalists and bloggers across Europe and parts of Central Eurasia. The Network Facilitator would operate out of the Network Hub from where they could provide the technical & legal support, cyber & physical security, funding and training for the network of actors.
In the scoping report the FCO recommended that the Network Hub be based in a secure central European city, for logistical ease as much as security. The EXPOSE network was also designed to act as a European online listening station reporting claimed Kremlin disinformation, which appears to be anything that disagrees with EU/NATO policy, back to the UK CDMD and FCO. Outlining the Facilitators role, the scoping report stated:
“The Network Facilitator will provide a centralised social listening function and media monitoring, tracking key disinformation narratives across Europe…….In turn, organisations will be provided with access to the latest social listening tools and training in how to use them………including mapping the sources and networks of these narratives and the audiences that are the most vulnerable to them………..This information can then be shared with the FCO, via the Network Facilitator ensuring that all data is gathered……”
The EXPOSE Network Facilitator
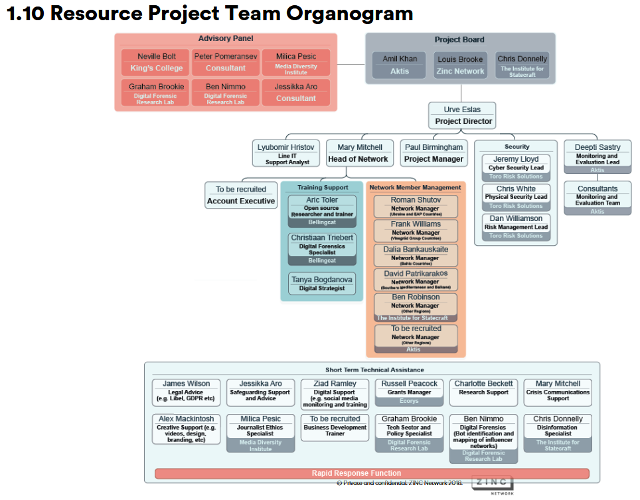
 The Network Facilitator contract was won by a consortium led by Zinc Network. They submitted their technical proposal on or after the 31st August 2019. We know this convinced the FCO to offer the Zinc consortium the contract. As with most contract bids, the FCO CDMD would have been interested to see what ‘added value’ Zinc could offer them. We cannot be certain which elements of that added value the CDMD, who maintain close control of the EXPOSE Network, chose to adopt. We can be more confident about the elements of the Zinc consortium are contractually obliged to deliver. These were specified in the scoping document and broadly outlined in the draft proposal.
The Network Facilitator contract was won by a consortium led by Zinc Network. They submitted their technical proposal on or after the 31st August 2019. We know this convinced the FCO to offer the Zinc consortium the contract. As with most contract bids, the FCO CDMD would have been interested to see what ‘added value’ Zinc could offer them. We cannot be certain which elements of that added value the CDMD, who maintain close control of the EXPOSE Network, chose to adopt. We can be more confident about the elements of the Zinc consortium are contractually obliged to deliver. These were specified in the scoping document and broadly outlined in the draft proposal.
The resource partners of the Zinc consortium are Bellincat, the Atlantic Council’s DFRLab and the Media Diversity institute. The main implementing consortium partners are the Institute of Statecraft and Aktis Strategy. Zinc Network are both resource and implementing partners. The consortium’s risk and security partner is said to be Toro Risk Solutions and the financial management of the Hub’s grant system is reportedly provided by Ecorys.
Zinc, Bellingcat, DFRLabs and the Media Diversity institute are the listed resource partners on the OIP website. There is further evidence that the Institute of Statecraft (in some form) and Toro Risk Solutions remain involved. However, the current status of the Institute of Statecraft is something we’ll discuss in Part 4. The role of Ecorys as possible grant managers is consistent with information released. Aktis Strategy, as a company, are definitely no longer involved, though former employees may be.
The Zinc Consortium Delivers
Anyone who reads the Zinc consortium’s (ZC) technical proposal can either see it as a perfectly legitimate and necessary addition to the UK’s national security effort or utterly horrifying, depending upon their beliefs. For all the reason we have previously covered, personally I find it chilling.
ZC state:
“We will mobilise a Network Hub based in London, led by an experienced Project Director, consisting of an agile team with core competencies augmented by a wider pool of vetted experts. Our approach is highly localised, based around regional clusters of actors who can collaborate to effectively undermine the disinformation ecosystem in their respective areas and engage audiences most vulnerable to disinformation.”
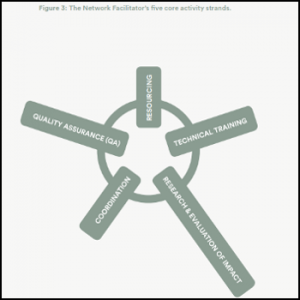 The Network Hub is the Open Information Partnership, currently represented by nothing more than single page website. The webpage is essentially a ruse (disinformation) to sell the idea that the OIP is a public, open and transparent organisation. It meets the FCO’s request that the operation be ‘overt’ and no effort be made to hide it. Like their suggestion that the Network Facilitator ‘assume’ autonomy, this looks like an attempt by the FCO to maintain “plausible deniability”. Noting this desire, ZC remark:
The Network Hub is the Open Information Partnership, currently represented by nothing more than single page website. The webpage is essentially a ruse (disinformation) to sell the idea that the OIP is a public, open and transparent organisation. It meets the FCO’s request that the operation be ‘overt’ and no effort be made to hide it. Like their suggestion that the Network Facilitator ‘assume’ autonomy, this looks like an attempt by the FCO to maintain “plausible deniability”. Noting this desire, ZC remark:
“To be sustainable and less vulnerable to attack from malign actors, the Network needs to be public-facing…… the strategy for public facing communications is based on minimum requirements, such as a static website……..The project could expand to build on this public facing component, promoting the network as a journalist integrity and disinformation network……Although the activities of specific Network Members will remain discrete, The Hub will be public facing, openly presenting itself as a project that brings together actors with a variety of expertise and interests in promoting media integrity across Europe. The positioning of the project in the broader media development and integrity sector is essential to help mitigate reputational risks both to the FCO and to safeguard the interests of Network Members.
Nowhere on the OIP single page website does it make any mention of the discrete nature of the wider network’s activities. Reputational management seems the sole reason for the webpage’s existence.
There is little doubt about the clandestine nature and precarious morality of the EXPOSE Network, openly addressed in numerous documents. In a bid to win the contract, ZC gave assurances to the FCO that their reputation would be protected:
“We will underpin activities with a robust risk management framework which takes as paramount the safeguarding of Network Members and other stakeholders as well as the potential reputational risks to the client (the FCO CDMD).”
[Note: Bracketed information added.]
ZC had good reason to manage risk in this way. They, or rather the people they train and support who form the ‘network of actors,’ are put in potential danger. The technical proposal is complete with case studies which reveal the ZC’s capabilities and experience of managing these risks:
“The Consortium established a robust safeguarding policy whilst establishing a network of YouTubers in Russia and Central Asia, who were creating content promoting media integrity and democratic values. This policy took measures to safeguard against Kremlin attack through actions including: supporting participants make and receive international payments without being registered as external sources of funding…….. and carefully managing project communications to keep their involvement confidential.”
Whatever you may think of the EXPOSE Network, while many names of those within the network of actors are now in the public domain, only those already identified as being part of the Network Facilitator, EXPOSE Network and the Open Information Partnership are identified in this series.
Zinc Consortium Are Watching You
As previously discussed, the purpose of the EXPOSE Network (hence the name) is to seek and identify those who are deemed to be peddling Kremlin disinformation. This essentially boils down to anyone who questions EU/NATO policies, narratives, actions or objectives. For example, Pro Brexit campaigners are cited as an ‘audience vulnerable to disinformation.’ The ZC spell out their strategy for dealing with such people. Their network of actors will be trained by ZC’s in-house digital experts:
“…….to map their target audiences online using leading social media mapping and listening tools, build targeting profiles, utilise social media advertising techniques to disrupt and divert vulnerable audiences away from disinformation.”

If this all sounds rather familiar it is because this activity is precisely the allegation leveled against the Kremlin by western states and the mainstream media. In seeking to defeat what they claim is Kremlin disinformation, the EXPOSE network is deploying the same operation they insist they are fighting against. Chicken and egg springs to mind.
ZC state they will:
“…..reach into all key target audiences, including not only media and policy makers, but also those most vulnerable to disinformation e.g. fringe media, far right or far left groups.”
As discussed in Part 2 none of these terms are clearly defined. Policy makers for instance could be anyone from elected politicians to committee members, advisers or think tank participants.
The ZC go further. They advocate targeting individuals and deploying behavioural change techniques. Alluding to the Behavioral Insights Team (BIT), the UK Government’s former in house ‘Nudge Unit,’ repurposed as a commercial enterprise in 2014, the ZC suggest applying psychological manipulation to change thinking.
“Cluster analysis will group individuals by attitudes, overlaid with traits (e.g. demographics, lifestyles, media consumption, cultural context), to create “personas”. These will be enhanced with behavioural insights gathered from qualitative research and/or linguistic analysis of online conversations to provide a 360 picture of:
- The individual context – Who the person is: values, attitudes, beliefs; self and social identity
- The cultural context – Who’s around them, what do they hear: community, influencers, social norms
- The environmental context – What do they experience around them, where are they in life: politics, economics, geography, media, comms/messaging, education/knowledge.
Understanding audience segments in this way will sharpen messaging frameworks, helping CSO partners to make the most of cognitive biases to target specific audiences, get maximum cut-through and resonance, and build stronger resilience to disinformation…….While the Terms of Reference focuses on organisations, we recommend expanding the scope to look at how to include the wider population, including small groups that may not be official organisations, individual activists, and concerned citizens”
The ZC were careful to couch this suggestion in terms of inviting individuals to join their counter disinformation effort. However, in the wider context of the EXPOSE Network’s obvious purpose, the implications are clear. The ZC were highlighting their capability to target concerned citizens.
We acknowledged in Part 1 that Russia run propaganda and disinformation campaigns. All developed nations do. However, there is no evidence that they are operating on anything like the scale of the EXPOSE Network. The strongest evidence released so far seems to show some very basic and largely ineffectual online adverting campaigns.
Whoever is labeled as a Kremlin disinformation agent, asset, troll or bot will then be reported by the ZC back to their FCO handlers in real time:
“Clear and consistent client reporting (to the CDMD) is essential to maintaining a strong and productive relationship with the FCO……Precise reporting requirements will be agreed with the FCO but we envisage will include: weekly status reports covering key outputs delivered by the Network, real-time generated data e.g. online reach and engagement, an updated risk register, plus any notable events….”
[Note: Bracketed information added.]
Using the raft of Internet ‘safety’ legislation currently being rolled out, EXPOSE Network ‘supporters’ like Google, Facebook, Twitter and others, can then be directed to purge the offending accounts. Along with the information, including any evidence, they direct the public towards. The Internet, as we know it, is increasingly being controlled. Access to information will be limited by the state and their corporate partners.
The EXPOSE Network Rapid Response
Speaking in June 2018, following the G7 summit, then UK Prime Minister Theresa May announced the G7’s Rapid Response Mechanism. The G7 stated that hostile state activity will be met with a rapid and unified response. Alleged hostile states will be identified for their ‘egregious behaviour’ and there will be swift, coordinated international attribution of guilt for cyber and other attacks.
Effectively they were declaring that foreign states will be blamed immediately for any event the G7 claims they are guilty of. No evidence or investigation required. Just arbitrary ascription of blame and rapid retribution. Apparently, this dangerous lunacy is part of the laboriously advocated ‘international rules based system.’ It appears to differ somewhat from International Law which focuses more upon concepts shunned by the G7, such as due process and evidence.

Earlier, in January 2018, the UK Government announced the creation of the National Security Communications Team (NSCT). This team of civil servants advise the Cabinet and Prime Ministers Office. Headed by Daniel Walpole, their role is to assist the UK Government with communications challenges related to national security, including (but not limited to) disinformation. In April 2018 they were joined by the Rapid Response Unit (RRU) who, in times of crisis, work closely with the NSCT.
The RRU monitors digital trends to spot emerging issues, including misinformation and disinformation, and identifies ways to respond. The Director of Government Communications Alex Aitken, speaking about the RRU, stated:
“Following the Syria airstrikes, the unit identified that a number of false narratives from alternative news sources were gaining traction online. These “alt-news” sources are biased and rely on sensationalism rather than facts to pique readers’ interest. Due to the way that search engine algorithms work, when people searched for information on the strikes, these unreliable sources were appearing above official UK government information…….The unit therefore ensured those using search terms that indicated bias – such as ‘false flag’ – were presented with factual information on the UK’s response. The RRU improved the ranking from below 200 to number 1 within a matter of hours”
The claim that only official UK Government information is factual and unbiased is both notable and demonstrably false. Yet it is Aitkens other claims about RRU/NSCT capability which are perhaps more interesting.

The process of Search Engine Optimisation (SEO) is a technique for creating content which ranks well for specific search or keywords. This involves ‘optimising’ for a whole range of ‘metrics’ which form the Google organic search algorithm (predominantly). An allegedly closely guarded secret, cracking the Google organic search algorithm is the holy grail for marketing companies the world over.
Even the WPP Group would struggle to take a web page’s organic Google search ranking from below 200 to number 1 in a few hours. What Aitken appears to reveal here is that the UK Government work with Google to fix the search results. Not so much a search engine, more of an official government statement website.
Google are prominent supporting partners of an array of EXPOSE Network partner organisations (see Part 4 and Part 5).
Advocating their Rapid Response vehicle the ZC offer the Counter Disinformation and Media Development Program the following service:
“….by coordinating members’ (network of actors) activities and resource to respond to pertinent anniversaries or events, such as the annexation of Crimea or local elections, or at flashpoints of disinformation. The Network Managers would coordinate this activity in their clusters accordingly, yet informed by a centralised strategy under the direction of the Project Director who will work closely with the FCO…….Our proposal already integrates a rapid response mechanism, facilitating a crisis response team comprised of technical experts with legal, security and communications expertise to support organisations at critical moments.”
[Note: Bracketed information added.]
A recent report by the internet market researchers SearchMetrics looked at how Google ranked a range of Brexit related Keywords. They clearly showed the overwhelming dominance of the UK state broadcaster, the staunchly pro EU BBC, in the search results, closely followed by the other mainstream media outlets. The BBC are tasked with propagating official government announcements. The BBC charter states the ‘public purpose’ of the BBC:
“To reflect the United Kingdom, its culture and values to the world: the BBC should provide high-quality news coverage to international audiences, firmly based on British values of accuracy, impartiality, and fairness. Its international services should put the United Kingdom in a world context, aiding understanding of the United Kingdom as a whole”
The BBC is publicly funded by license payers and that fee is controlled by government legislation (2003 Communications Act). Their funding settlement is set by the UK Secretary of State. Like the EXPOSE network, they are a UK government department in all but name.
Seeing as the UK government appear to be in partnership with Google, who dominate the Internet search market, the BBC’s near monopoly of search results related to contentious political issues isn’t surprising. It is now possible to envisage how the Rapid Response Mechanism will work from the public’s perspective.
The G7 will blame another country for some event or crisis. Claims of cyber attacks, the evidence for which is ‘virtual’, are extremely vulnerable to state manipulation. Currently it appear most likely that either Russia, Iran or China will be blamed should a cyber attack occur. However, it could be any foreign power that falls into the G7’s cross-hairs. Yemen maybe? Blame will be attributed without any investigation or any need of proof. Evidence is irrelevant.
This will be accompanied by a slew of ‘counter disinformation’ content pumped out by the EXPOSE Network. They will also rapidly identify anyone who questions the G7’s assertion. The ‘counter disinformation’, accurate or otherwise, will support the G7 narrative without question.
Governmental communication strategists in groups like the UK’s NSCT and RRU will then work in partnership with the major search engines, MSM outlets and social media partners to ensure the G7 message is ubiquitous across all platforms. Elevating EXPOSE content and other approved information via a network of ’embedded’ journalists and MSM assets. Meanwhile, based upon information received from the EXPOSE Network, any dissenting voices asking questions or advocating restraint will be ‘down graded’ and relegated to relative information obscurity.
It appears that dissent will not be tolerated.
The EXPOSE Networks Proposed Election Strategy
The recent Mueller Report, in the U.S, into alleged Russian ‘hacking‘ of the 2016 election failed to produce any substantial indictable evidence to prove the allegations of Russian interference, or state collusion. A small team of Russian trolls on social media is hardly a threat when faced with the magnitude of an operation like the EXPOSE Network.

We don’t know if the FCO CDMD authorised the ‘added value’ offered by the ZC, only that they offered them the contract. However, if they did, then clearly meddling in elections is firmly on the EXPOSE Network’s agenda:
“Elections are often a flashpoint for disinformation ……the Network could focus project resource on elections taking place in countries that are of particular interest to the FCO. The Network would…..monitor the online communications around the election three months ahead of the event, identifying key trends and flashpoints in activity or narratives. This activity could be intensified six weeks prior to the election itself…….. The team could test different approaches to engage targeted audiences through mainstream media or governments……..We could also work with social media providers……We could also build some Network Members into a longer-term election cluster of organisations who prioritise this in their routine activity.”
It is difficult to imagine how a propaganda operation of such ambition could possibly deliver on a budget of £10 million over three years. Of course it can’t and were its budget truly £10 million it wouldn’t. However, potentially available government funding is far in excess of this amount. The CDMD is funded by the UK Conflict Stability and Security Fund (CSSF). They alone have an annual budget of £1.3 billion. Yet there is far more European state funding than that on the table. We discuss this in Part 6.
It isn’t just governments who are attracted to the EXPOSE Network either. Adding further value to their bid, the ZC stated:
“Zinc will also encourage other donors to provide additional financial resources to the Network and the wider sector.”
The EXPOSE Network’s listed partner organisation are collectively funded by a huge international network of governments, NGO’s, philanthropic foundations, wealthy individuals and multinational corporations. Acting collectively in support of the EXPOSE Network, available resources are feasibly limitless.
It is this interconnected web that we’ll begin to explore in Part 4.








Be the first to comment on "EXPOSE Network and the Open Information Partnership – Part 3"